Defense in Depth: A ‘layered’ strategy can repel the hordes of hackers
A holistic security infrastructure can defeat the cyber criminals trying to break into your systems
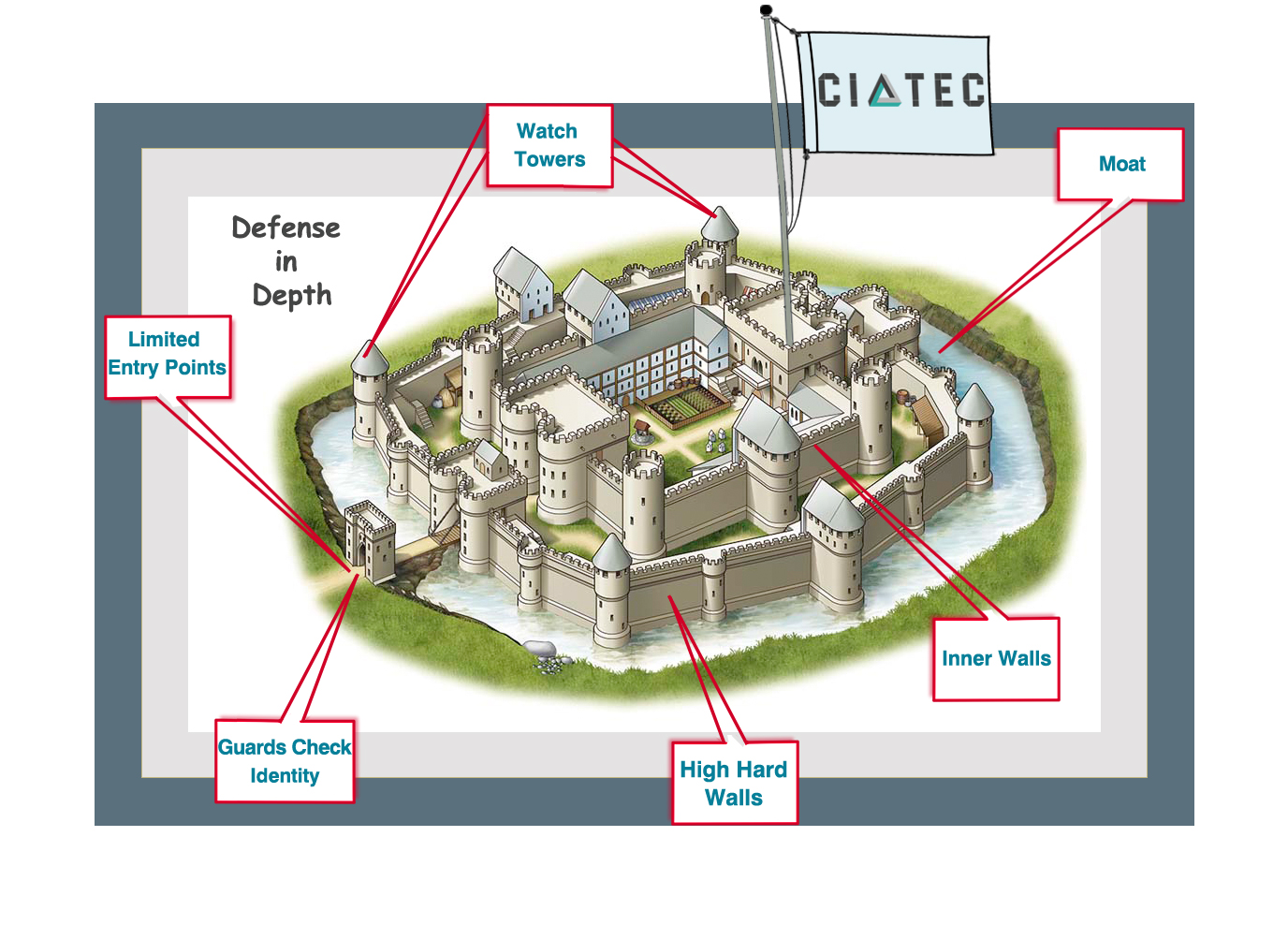
The Origin of Defense in Depth
The notion of in-depth defense originates from the military model, which demonstrates that it is far more difficult to penetrate multiple layers of physical or non-physical defenses, than to simply break through a single line of defense. It is clear that an organization’s information property and resources can only be safeguarded if a number of security measures are used concurrently to this end.
Why Defense in Depth?
Although it is impossible to protect IT systems against all hackers, a sophisticated and effective in- depth system can assist IT administrators and security departments to detect and name hackers who are trying to breach the security of a computer, a server, a network or an ISP. Should a hacker manage to get through the first line of defense, and gain access to the system, an in-depth defense system can neutralize this threat long enough for network specialists and system administrators to ensure the breach does not happen again. This can be done by strengthening measures used to negate and counter the effects of the hacking.
An effective in-depth defense model will exploit the opportunities offered by slowing down the developing threat – and this ability is a key element in protecting information assets. An early warning system will come into play immediately attacks and issues are detected, so that a rapid response can be deployed, countering the threat’s effects by activating a damage limitation strategy. In this way, any non-technological measures which need to be introduced in response to the threat can be set in motion before the full impact of the threat can develop.
Components and layers of defense in depth include:
- Applications
- Data Access Layer
- Platforms
- Servers
- Operating Systems
- Networks
- Demilitarized Zones
- Data Repositories
The following are examples of techniques that can be used to implement defense in depth:
- Authentication and Authorization
- Anti-Virus Tools
- Intrusion Detection
- Encryption
- Firewalls
- Sandboxes
In addition to electronic countermeasures, physical protection of business sites along with comprehensive and ongoing personnel training and situational awareness enhances the security of vital data against compromise, theft or destruction.
Defense in depth strategies also include other security preparations than directly protective. They also address such concerns as:
- Monitoring, alerting, and emergency response
- Authorized personnel activity accounting
- Disaster recovery
- Criminal activity reporting
- Forensic analysis





